Secure Shell (SSH)
It is a cryptographic network protocol used for securely communicating with another computer.
It allows us to login into a remote machine and execute commands on it.
It uses TCP port 22.
SSH is based on a Unix shell, therefore standard Unix commands can be used to view, modify, and transfer files from a remote machine once an SSH connection has been established.
Uses
- For login to a shell on a remote host (replacing Telnet and rlogin)
- For setting up automatic (passwordless) login to a remote server.
- For securely mounting a directory present on a remote server as a filesystem on a local computer using SSHFS.
- For forwarding or tunneling a port
- To transfer files using the associated SSH file transfer (SFTP) or secure copy (SCP) protocols
How Does SSH Work?
Understanding Different Encryption Techniques
To secure the transmission of information SSH uses three different encryption:
- Symmetrical encryption
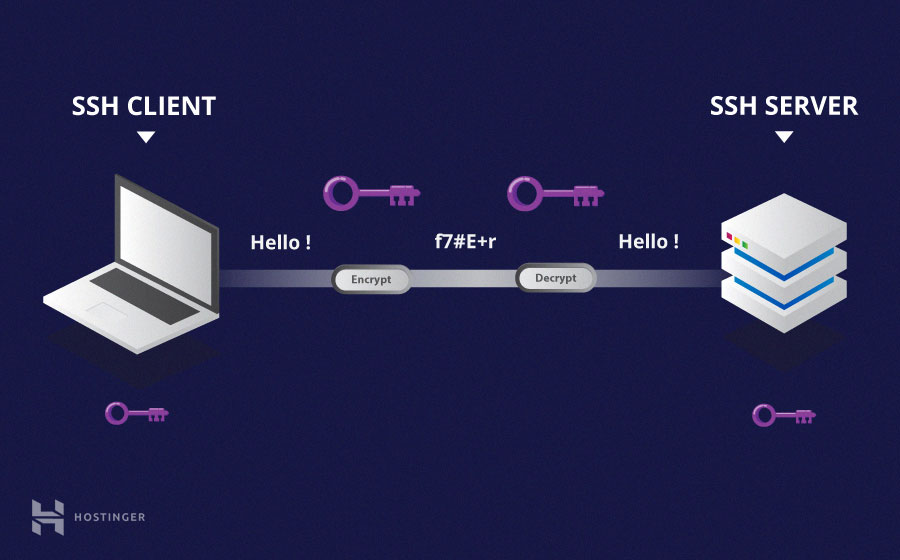
In it a single key is used to encrypt and decrypt the messages.
It's also called “shared secret” encryption, or “secret key” encryption.
SSH use these keys in order to encrypt the entire connection.
Secrety key is generated prior to client authentication.
Key Exchange Algorithm
The client and server both contribute to establish this key through a process known as a key exchange algorithm.
The key is never transmitted between the client and the host. Instead, the two computers share public pieces of data and then manipulate it to independently calculate the secret key.
Before establishing a secured connection both client and server (host) decide which cipher to use like AES, Blowfish, 3DES, CAST128, and Arcfour.
- Asymmetrical encryption
In it two separate keys are used for encryption and decryption.These two keys are known as the public key and the private key. Together they form a public-private key pair.
The public key can be freely shared with all parties. It is associated with its private key and the private key cannot be derived from the public key.
A message that is encrypted by a machine’s public key, can only be decrypted by the same machine’s private key.
Meaning that the public key can not decrypt the messages it encrypt.
Therefore server and client use each others public keys to encrypt the message and decrypt it with their own private key.
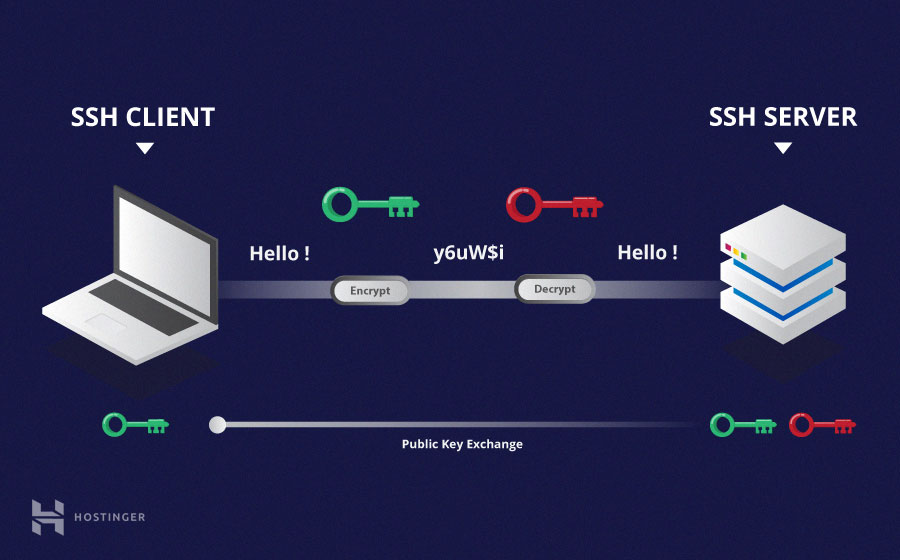
Usage
- This encryption is used during the key exchange algorithm of symmetric encryption. Before initiating a secured connection, both parties generate temporary public-private key pairs, and share their respective private keys to produce the shared secret key.
- These key pairs can be used to authenticate a client to a server instead of password. The client creates a key pair and then uploads the public key to the server. This is placed in a file called authorized_keys within /home/user/.ssh directory on the server and server's public key is stored in known_hosts file in .ssh directory on the client.
- Hashing
SSH uses One-way hashing .One-way-hash are not decrypted.
SSH uses hashes to verify the authenticity of messages. This is done using HMAC (Hash-based Message Authentication Codes). This ensures that the command received is not tampered with in any way.
How it is done?
-
A MAC algorithm produce Message Authentication Code (MAC) from a message and a secret key for security as it is impossible to produce the MAC of a message and a secret key without knowing the secret key.
-
Then the key and the message are concatenated (joined) and hashed together and called HMAC.This makes it impossible to find the key as hash cannot be reversed.
An HMAC is a MAC which is based on a hash function.
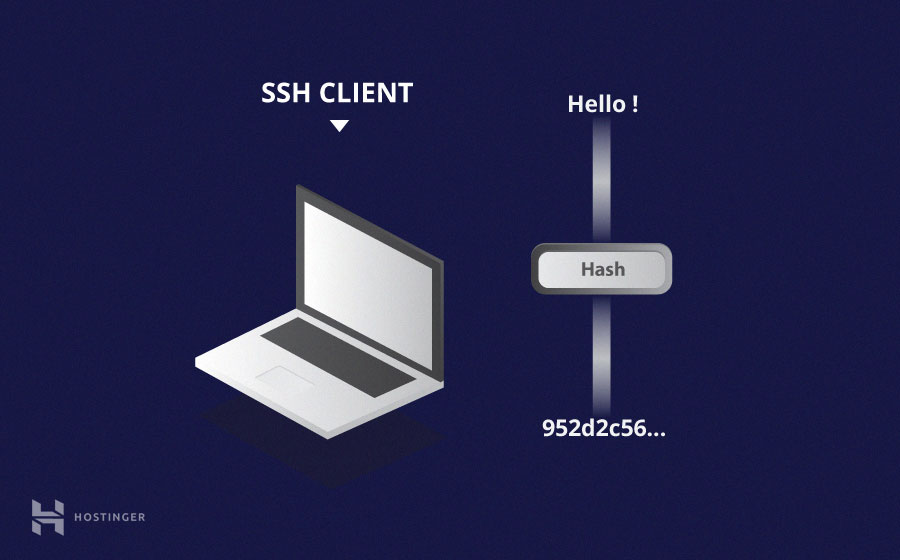
It is easy to generate a cryptographic hash from a given input, but impossible to reverse it (generate the input from the hash). This means that if a client holds the correct input, they can generate the crypto-graphic hash and compare its value to verify whether they possess the correct input.
Working
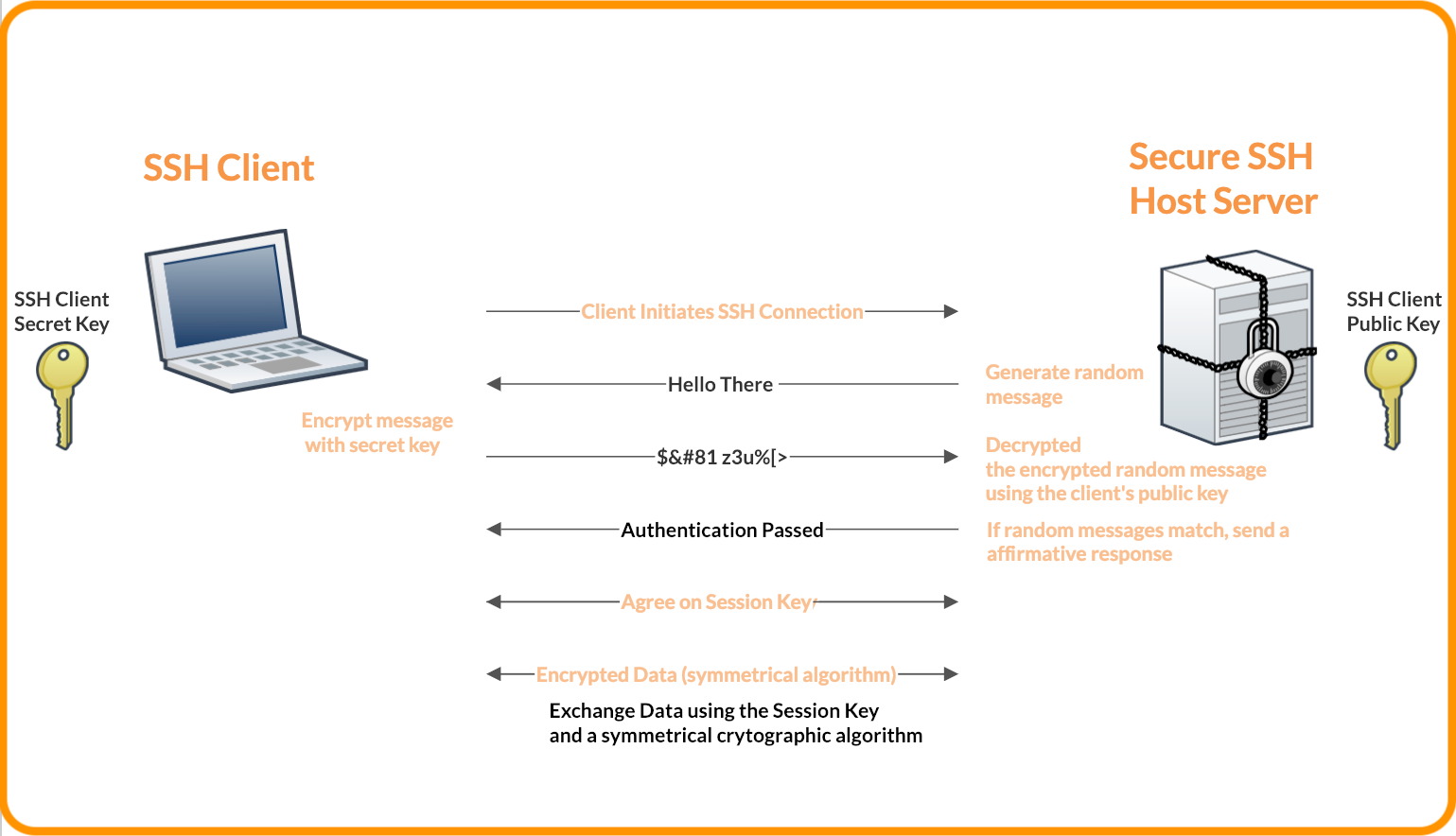
SSH uses the client-server model.
The host (server) listens on SSH assigned port or 22 for incoming connections.
It organizes the secure connection by authenticating the client and opening the correct shell environment if the verification is successful.
The client begins the initial TCP handshake with the server, negotiating the secure connection, verifying that the server’s identity matches previously recorded information (recorded in an RSA key store file in .ssh directory), and provide credentials for authentication.
An SSH session is established in two stages:
- The first stage is to agree upon and establish encryption to protect future communication.
- The second stage is to authenticate the user and discover whether access to the server should be granted.
- Session Encryption Negotiation
When a client tries to connect to the server (via TCP), the server presents the encryption protocols and respective versions that it supports. If the client has a similar matching pair of protocol and version, an agreement is reached and the connection is started with the accepted protocol.
The server also uses an asymmetric public key which the client can use to verify the authenticity of the host.
Once this is established, the two parties use what is known as a Diffie-Hellman Key Exchange Algorithm to create a symmetrical key. This algorithm allows both the client and the server to arrive at a shared encryption key which will be used henceforth to encrypt the entire communication session.
- Authenticating the User
The user is asked to enter the username, followed by the password. These credentials securely pass through the symmetrically encrypted tunnel, so there is no chance of third party sniffing but bots can simply brute force easy or default passwords and gain access.
Therefore, it is recommended to use SSH Key Pairs.These are a set of asymmetric keys used to authenticate the user without the need of inputting any password.
Versions:
- SSH-1 = First release
- SSH-2 = It is incompatible with SSH-1. It features both security and feature improvements over SSH-1.
- OpenSSH = It is the open-source version and the most popular SSH implementation used by Windows 10.
SSH In Action
-
For connection ssh uses symmetric encryption and hash (HMAC) and for authentication ssh uses asymmetric encryption.
-
Public-Private Key pairs are generated on both client and server independently and not over the network.The public keys from these pairs are shared over the network.
If key based authentication is used.
Syntax:
To connect to a system:
ssh [USERNAME]@[TARGET IP]
To specify a port, use -p [PORT]
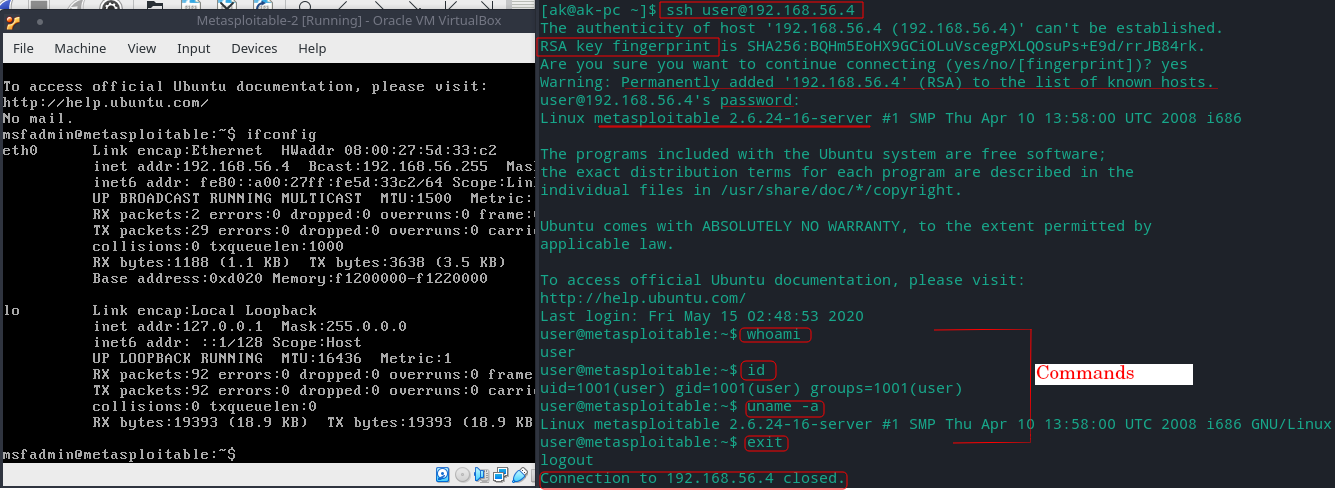
Here we are connecting to a Metasploitable2 server (left) using ssh command with username ‘user’ (right).
First the RSA public key of the server is saved in known_hosts file in .ssh directory because we are making connection to the server for the first time.
After that we enter password for ’user’
and execute some Linux commands to get information about user and the server.
Behind the scenes with Wireshark
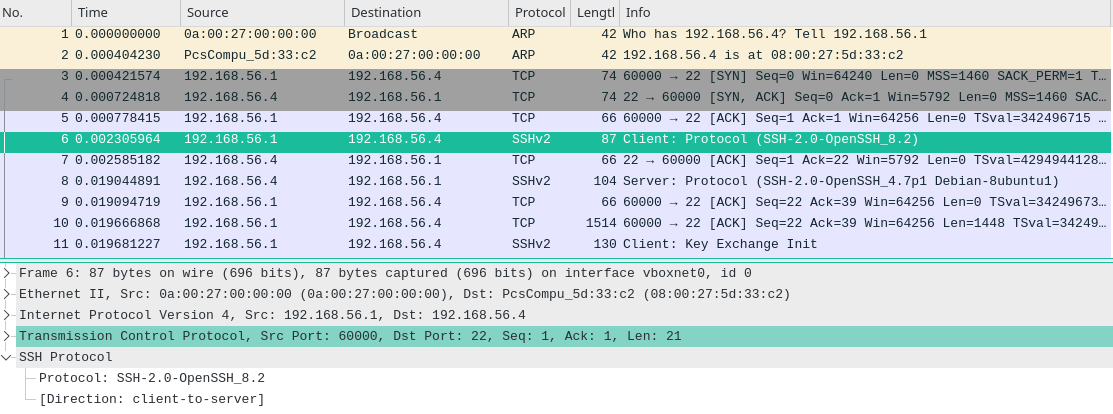
- The client (our machine) begins the initial TCP handshake with the server and sends SSH connection request to the server and the client is running OpenSSH v8.2.
Note: SSH-2 and OpenSSH are essentially the same.
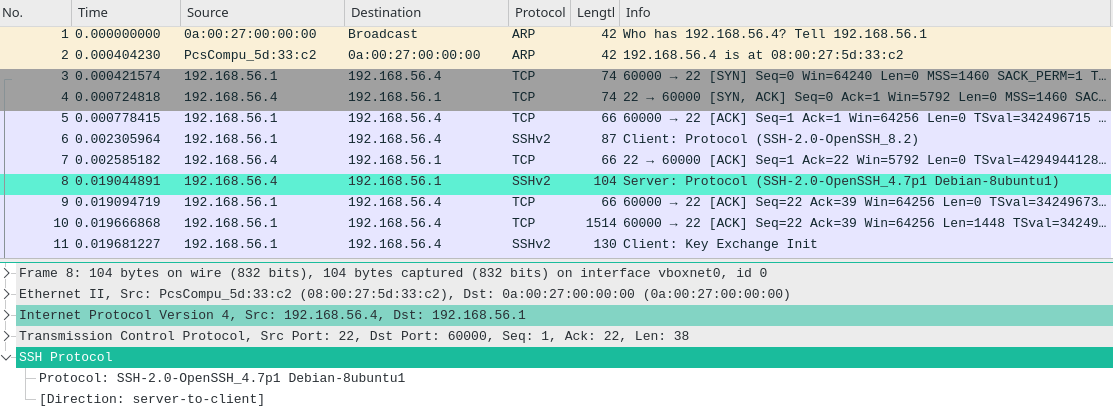
The server is replying to our request using OpenSSH v4.7p1 and now we also know that server is based on Ubuntu or Debian.
- Here, the client tells the server the algorithms it supports for each function (encryption, MAC, key exchange, host authentication, compression) in order of preference.

The server will send us it’s list.
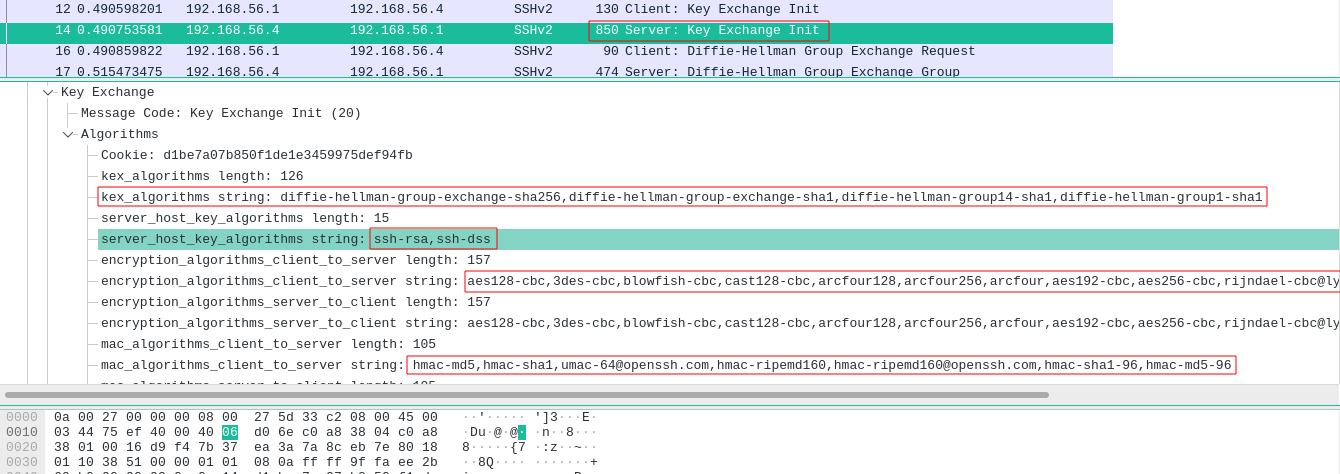
From the two lists of algorithms the same key exchange algorithm will be used.
- Now following packets will be shared between both machines:
SSHv2 Client: Diffie-Hellman Key Exchange Init
SSHv2 Server: Diffie-Hellman Key Exchange Reply
SSHv2 Client: Diffie-Hellman GEX Init
SSHv2 Server: Diffie-Hellman GEX Reply
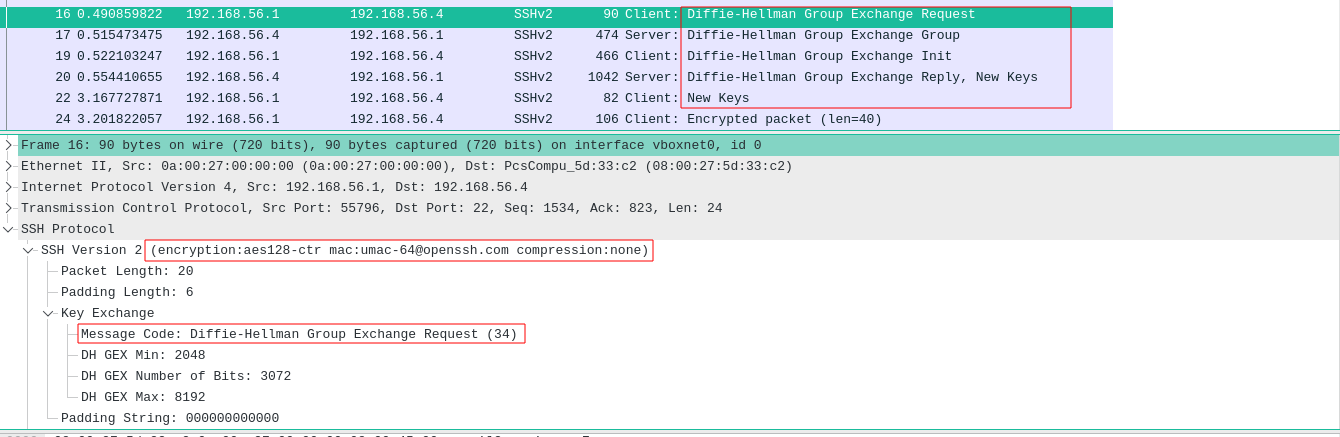
Above we can see that,
This SSH session will be using AES-128bit in Counter mode for symmetric encryption with an HMAC based upon MD5 to ensure message integrity.
and
Diffie-Hellman Key Exchange Algorithm is used to create the symmetrical key (shared secret).
- The shared secret encryption that is used for the rest of the connection is called Binary packet protocol.
- The shared secret is then used to encrypt all communication that follows.
- After the session encryption is established, the user authentication stage begins (Step 5).
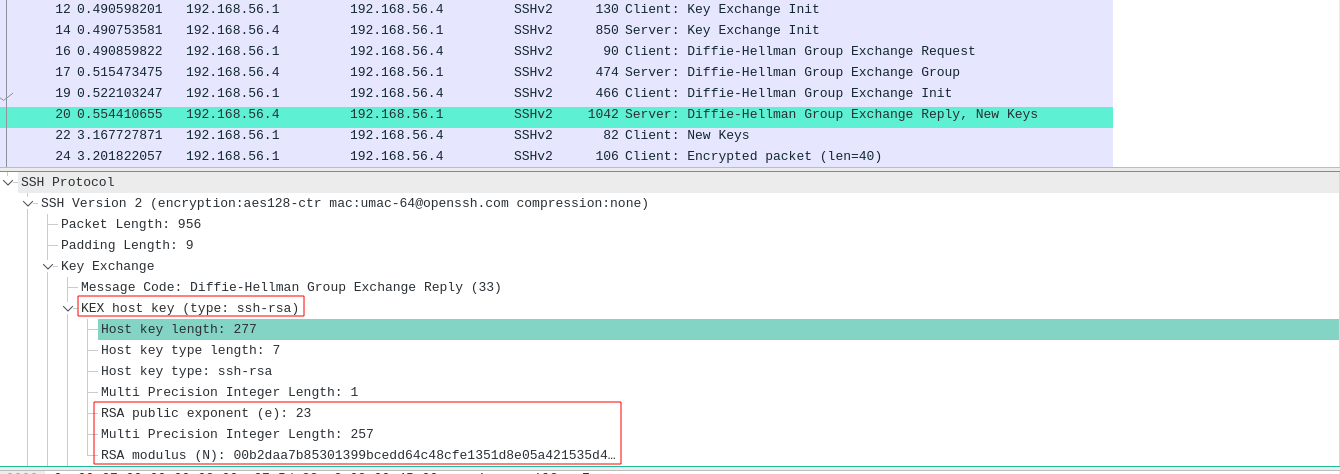
Note: The reply of the server also contains it’s public host key (identity) or certificates. If the client has never seen it, the client usually asks the user if it should trust it (The RSA key fingerprint in the beginning).
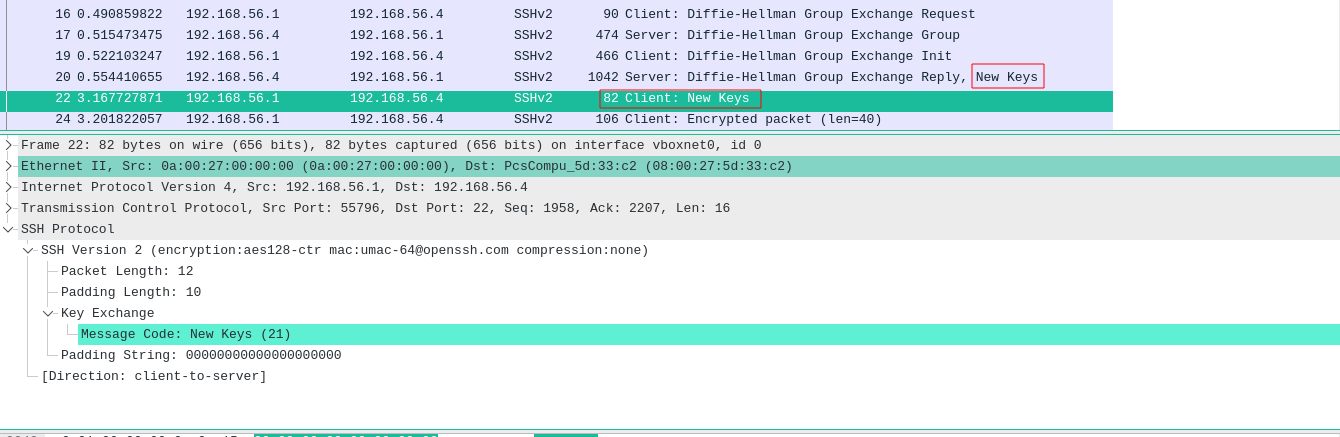
- New Keys is an acknowledgment that both will use the same key for communication.
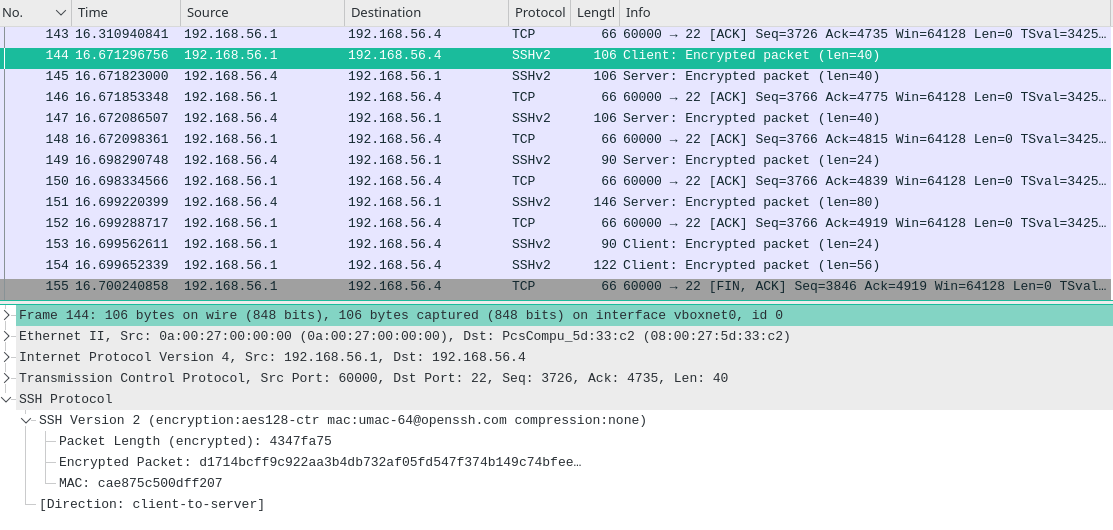
- All the data sent by client to server will now be encrypted including the user password and commands like whoami,id,uname -a and exit.
Below we can see servers public key stored in our machine (in .ssh/known_hosts) and user's public key in server (in .ssh/authorized_keys).
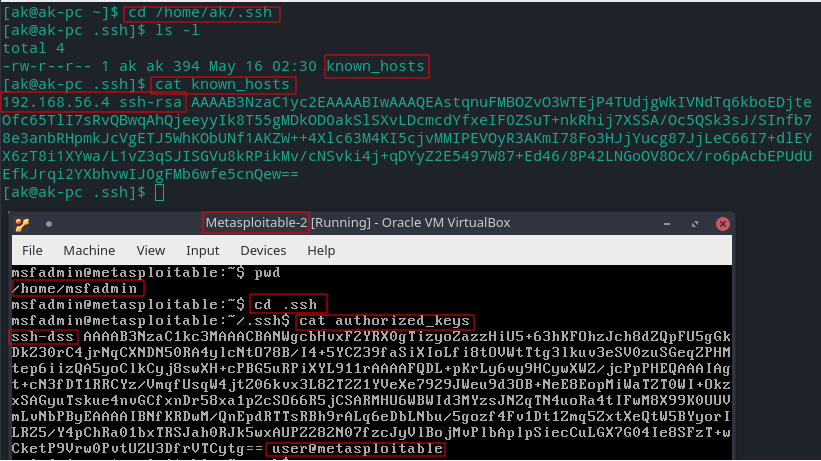
SSH can use either "RSA" (Rivest-Shamir-Adleman) or "DSA" (Digital Signature Algorithm) keys.
RSA (Rivest-Shamir-Adleman) is an asymmetric cryptographic algorithm used by modern computers to encrypt and decrypt messages.
DSA is not used anymore as it is less secure.
DSS(Digital Signature Standard) is simply a document that describes the signing procedure and specifies certain standards.
Note: The DSA key present on Metasploitable2 (server) are not generated by our client but we can use it for SSH connection. The key was generated by a client called user and we were able to use it because it is stored in authorised_keys means anyone who know password for user can connect to the server using any machine.